The idea for this post sparked from a recent conversation I had where a non-computer savy friend of mine asked me, "What can I do to be more secure from hackers?" After giving him a few general purpose tips, such as use a VPN or have an AV installed, he said "Ok, but I want to know more about the wierd and oddly specific attacks someone could do against me." So after a while of talking here are some of the oddly specific, yet actually useful tips that could come in handy when trying to be more technologically secure.
1. Get rid of your RFID-enable credit cards

If you are one of the lucky people that have been given an RFID-enabled credit card, you should highly consider giving that back (or if you are feeling adventurus you could puncture a the RFID chip) . First of all, it's completely unnecessary since swiping a card doesn't take THAT much more time to do. Second of all, they are easily clonable. With roughly $200-$300 worth of equipment you could easily sniff and clone one of these cards. If you want to know a bit more in detail about RFID technology feel free to check out my previous post about it.
2. Turn WPS off
For some bizarre reason, routers today come with something called WPS enabled by default. This is something meant to make connecting to them easier, but the truth is that I have yet to meet someone who has ever used WPS to connect to their router. The funny part is that having this enabled makes it substantially easier for a hacker to break into your Wi-Fi. Turning WPS will vary slightly depending on your router, but the overall process consists in:
- Go to your routers address (usually 192.168.0.1 or 192.168.1.1)
- Log in with your credentials.
- Somewhere in there (usually Wireless tab) will have an option to turn WPS on/off
Note: If in step 2 you used the routers default credentials, you should definitely change those too.
3. Avoid "Master" branded locks
If you have something physical that you want to keep safe, you should probably not use Master locks. At DEFCON, when I asked the lockpick experts of TOOOLS to teach me how to lockpick, the first thing they told me was to practice with Master branded locks, because they suck. Turns out that without any previous lock picking knowledge, it took about 30 minutes to crack it open. After I got the hang of it, they would pop open in at most 3-5 minutes. So if you really want to keep something secure try shelling out a couple of dollars more for a better lock.
4. Check if you've been pwned
Now-a-days, even if you are super safe and use super awesome passwords with uppercase letters, numbers, symbols, haikus and one aromatic fragrance, some company will most likely slip up and your password will be revealed. It's just a fact of life; someone somewhere will hack some database and sell your carefully chosen password to some sketchy hackers somewhere. The best way to deal with this is to check if your credentials have been compromised with haveibeenpwned.com. You can check if your credentials have been leaked, and you can even subscribe to them so that they keep an eye out and notify you in the future.
5. Set Automatic Updates
Sorry if this is an obvious one, but let's be honest, we've all done that thing where we tell Windows, OSX, Android, iOS, or whatever OS you have, to stop bugging us and don't update. We'll turns out that's a terrible idea. You should most definitely, keep your things updated. Here's why: Unless you are a very high profile person, the hackers that are attacking you are probably not that dedicated, they will most likely piggyback off published scripts and known vulnerabilities. They can do this by just looking through exploit databases such Rapid7's DB. However, if you have everything patched and updated, you'll make their work a bit harder, thus they might just get bored and move on to someone else. For example, it is well known that old versions of adobe acrobat have vulnerabilities where one can craft a malicious pdf that will inject code into your computer. If you have your adobe acrobat updated to the latest version, you have to worry about one less thing!
6. Update Firmware on Logitech mouse/keyboards
Following a bit behind #5. If you have any Logitech wireless mouse/keyboards you should most definitely update their firmware. Recently, a vulnerability called Mousejack was discovered where people can inject keystrokes or eavesdrop what you are typing. I recently bought a couple of used keyboards/mice and have been playing around with it and was surprised at how easy it was to hack it. If you are using the latest Windows 10, you shouldn't encounter any problem, however OSX and Linux are (surprisingly) still vulnerable, so your best bet is to update your keyboard/mice firmware. I'll probably post more hacky details about this later 🙂
7. Trash Emails
A lot of people have trash emails to subscribe to shady websites, however I found these types of emails particularly useful when you want to use computers other than your own. There was a small cyber-cafe at my previous apartment housing which contained some of the most ill secured computers I have ever seen. Since I could print freely in there I realized I needed a one way trash email, one that I could send my schoolwork to print and wouldn't mind getting hacked. If you do it with gmail.com, you might even want to set up a google drive folder with read-only privileges for it.
Optionally, if all you really want is a trash email for sketchy subscriptions you should probably be using 10minmail.com. This is literally a mail service where you are given an email address that will only live for 10 minutes.
8. Avoid Phishing
Phishing comes in all shapes and sizes. Phishing is a type of attack were a malicious attacker will send you an email that seems to be coming from a legitimate source requesting some type of personal information (or contains infected links or files). There are a couple of ways to spot these emails:
- Hover over links before clicking. You always want to make sure that the link is actually going where it is supposed to go to. For example: They could try a switch and bait such as www.google.com or if you see a link like facebook.konukoii.com you should now that you are actually connecting to konukoii.com as opposed to facebook.com (You might think this is obvious, but it's easy to miss if it is something like facebook.mailservice.com or some other unsuspicious domain name).
- Check who really sent the email. A fantastic way to determine the legitimacy of an email is to check who sent it. Some modern mail servers such as gmail allow you to see the exact email from who sent it (example below). While other's like Outlook don't do this by default, instead you have to select your email and click on the option to view source.
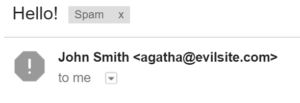
- Check the source if you are really suspicious. Usually by following the previous points you will have a good idea of whether or not an email is legitimate, but if you want to go into more detail, there is usually an option in email clients to "Check the Source" or "View original". This will give you all the information including the mailservers sent from.
9. Lock your BIOS or Keylog your own machine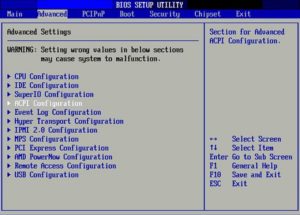
This point is particularly aimed at paranoid users who are concerned over someone getting physical access to your computer. When your computer boots up, there is a small component called the BIOS which is in charge of telling the computer where to boot from (aside from many other things). If someone wanted to be really sneaky they could turn your computer on and run linux from their pendrive, then access your harddrive and perhaps steal some of your files. The only true way to stop this attack would be to go into your BIOS (usually by pressing F1 before Windows boots) and then eliminating the option of booting from USB. Furthermore to avoid someone changing these settings you have to password protect your BIOS. This will change depending on your computer, so it's best to search online how to access your BIOS; Once there, the rest should be pretty self explanatory.
You might say, "Hey! but I still don't feel protected". Well, a nifty solution could be to keylog your own computer, such that you could know if someone is messing with it and see exactly what they are doing. Check out the "Capture the Keys" posts I have if you are interested in building your own keylogger.
10. Really format your hard-drives

When you are getting rid of an old computer, or throwing away a hard drive, it might be in your best interest to "really" format your HD. Most file systems work by having an index that points to all your files, so when you format a HD, it simply erases that index, while leaving the actual information in the disk. I was suprised to discover that data recovery from a "formatted" HD is extremely easy. However, you can really format a HD by using program such as DBAN. Alternatively, if you are throwing away the hard drive, you can smash the plates inside.
11. Don't use random pendrives (You don't know where they've been).
In real life, another attack vector consists in leaving behind "lost" pendrives or CDs in the hopes that someone will plug them into their computers. Once connected, they hope that you open an infected file. Or if you are one of the few people that have autorun set up then you probably are screwed as soon as you plug that pendrive in. A good Antivirus and a properly patched system should be enough to protect the average Joe, however if you want to be extra safe, don't go plugging in any random pendrive in your PC.
Also, as a bonus comment, there is a special kind of pendrive called a USB Kill that will permanently damage your computer as soon as you plug it in.
Bonus: The typical tips
You should know, or at least heard, of these by now:
Use an AntiVirus: This shouldn't be a tip, since you are smart enough to know you need an antivirus, regardless of operating system. At the very least they are useful to hold back script kiddies. When in doubt about a particular file, use VirusTotal.- Use a VPN: This protects you from unwanted sniffer looking at your internet traffic while you are connected to a public Wi-Fi. The best one I've found so far is Private Internet Access
- Use a cloud service to store important files: That way if you get hit by ransomeware or some other nasty virus, you can erase everything and start over without loosing any important files. The service you use depends on what you need it for, but as always there is a bunch of options: Dropbox, Amazon Cloud Store, Google Drive, etc.
- Encrypt your important files: You can use many different tools to keep your important files secure. You should really be doing this for important banking, financial, etc. documents. Lifehack did a good post on some tools for this.
Recent Comments